IDENTITY & ACCESS MANAGEMENT
Identity as a service (IDaaS) enables your organisation to securely connect the right people to the right technologies at the right time - all from the cloud.
Modern cloud identity solution for modern companies
Secure
Secure, centralised and
seamless access to all enterprise applications.
flexible
Subscription-based and thus scalable and cost-flexible.
Efficient
Enormous time savings, e.g. in the creation and removal of user accounts.
What is it about?
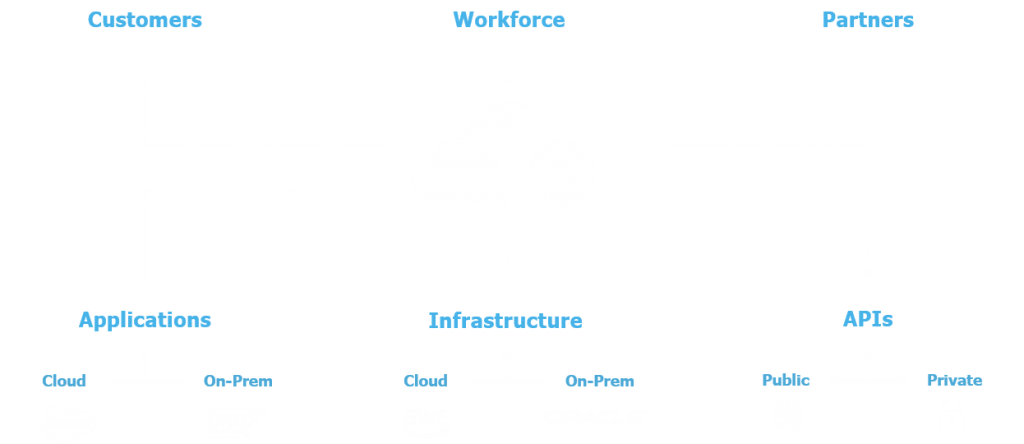
The goal of reliable identity and access management is to ensure that users are who they say they are and to give them the right types of access to applications and tools at the right time. The service helps organisations control who their organisation's users are (identity component) and what services they can or cannot access as well as how they can access them (access management component).

The identity challenges are growing
- As an organisation scales, the number of tools and applications in use increases, and so does the burden of managing login credentials across a wide range of team members, platforms, and devices.
- Identities and users are now the main target of attacks and the (data protection) risk continues to increase.
- Security failures can threaten the existence of an entire company.
- Manual tasks - such as resetting passwords and setting up accounts, are enormously time-consuming and prone to error.
Advantages of IDaaS solutions
Directory
You can customise, organise, and manage any user attributes from multiple identity sources with a flexible, cloud-based user store.
Single Sign-On (SSO)
Free your employees from multiple and lengthy passwords. With a single set of credentials, they can access enterprise applications in the cloud, on-premise, and on mobile devices.
Multi-factor authentication (MFA)
Secure apps and your virtual network (VPN) with a resilient policy framework, a comprehensive set of advanced verification factors, and adaptive, risk-based authentication that integrates with all your apps and your organisation’s infrastructure.
Lifecycle management
Automates the onboarding and offboarding of users, for example, by ensuring seamless communication between directories such as Active Directory and LDAP and cloud applications such as Workday, Office 365 or RingCentral.
commehr and Okta for your identity solution
commehr supports your company throughout the entire implementation of Okta - from the initial consultation to daily support. Translated with www.DeepL.com/Translator (free version)
One platform for all use cases